See your Cryptography. Secure your Future.
The only platform that discovers, inventories, and enriches cryptographic assets with business context — so you can fix what matters.
Why Enterprises Need Cryptographic Discovery, Inventory and Risk Assessment
Encryption is everywhere — TLS/SSH, key management systems, HSMs, APIs—yet most organizations can’t see the full picture. With the threat of harvest-now-decrypt-later and rising compliance pressure, cryptographic visibility is no longer optional. Qinsight shows where encryption is used, how secure it is, and what must change to be ready for the post-quantum era.
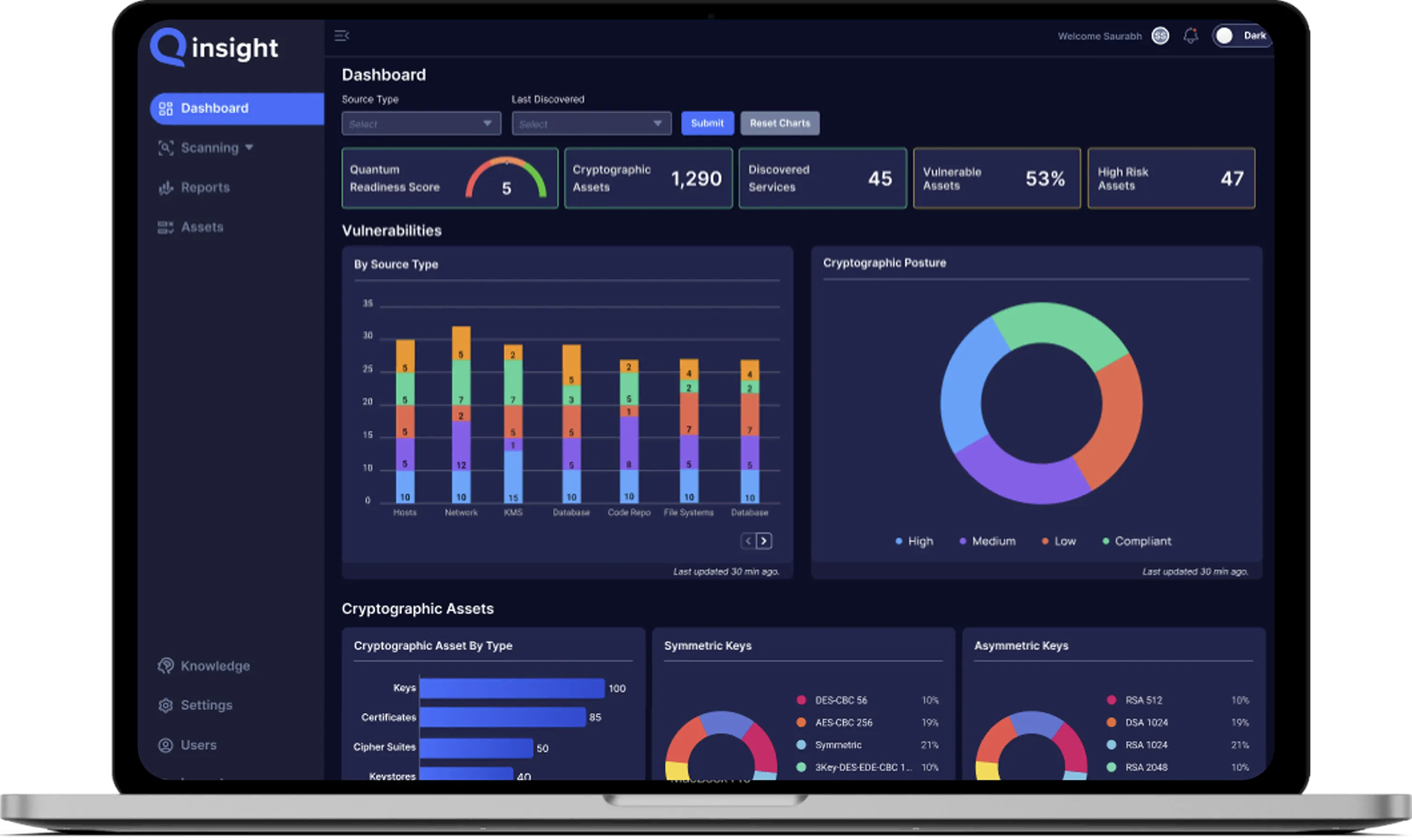
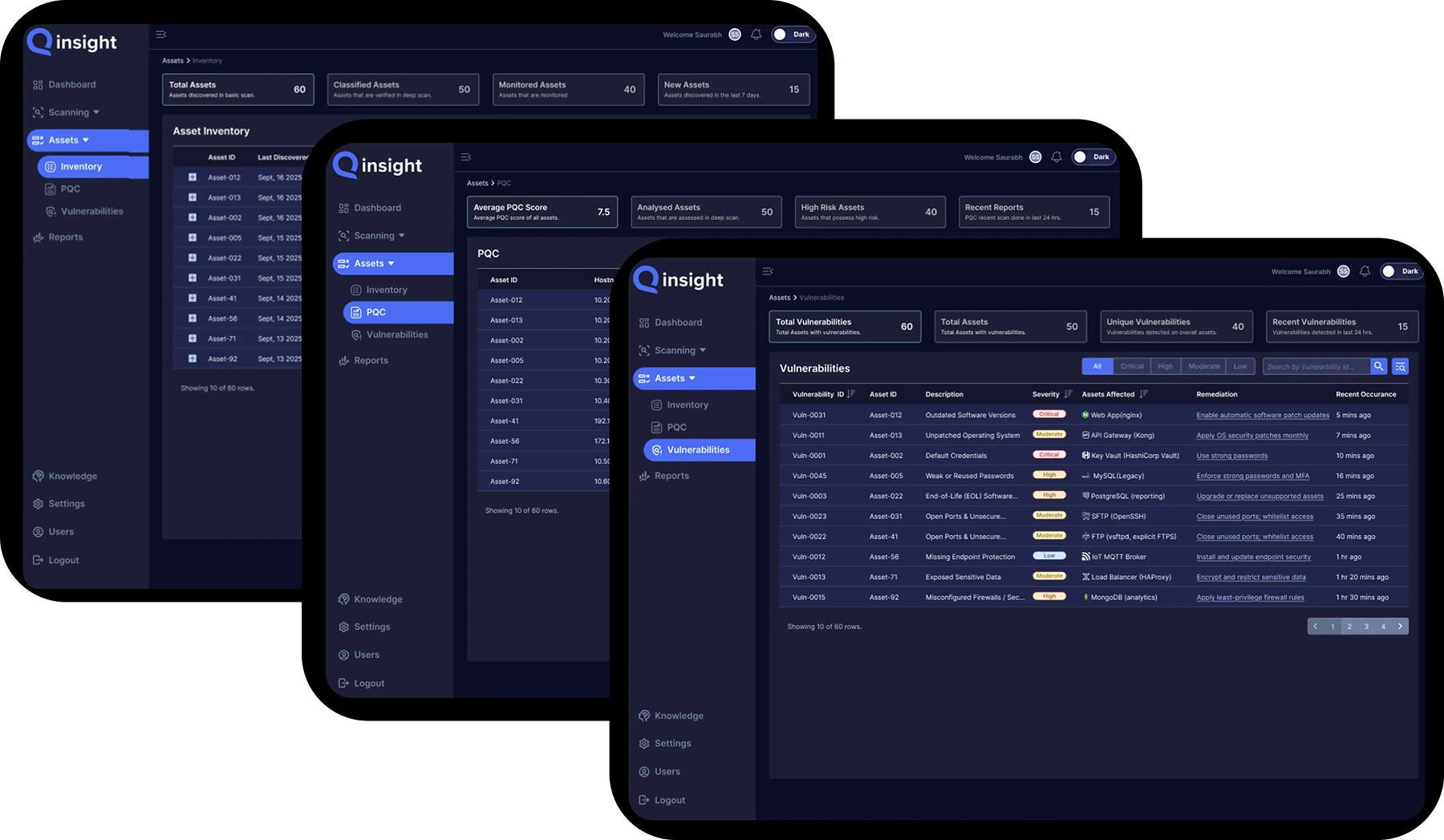
Key Features of a Cryptographic Posture Management Platform
Improve Cryptographic Posture
Fully Visibility
Gain complete insight into all cryptographic assets across your enterprise environment.
Continuous Monitoring
Detect changes in cryptography in real-time to maintain ongoing protection and compliance.
Improve Security
Identify weak or expired encryption, keys, and certificates before they become exploitable.
Reduce Downtime
Prevent service outages by proactively managing expiring ceritifcates and crypto dependencies
Quantum Readiness
Assess exposures to quantum-vulnerable algorithms and plan migration to post-quantum standards.
Ensure Compliance
Meet evolving regulatory and industry mandates through automated crypto audits and reporting.
Who Needs a Cryptographic Posture Management Platform?
Financial Services
Identify and mitigate cryptographic risks across payment systems, trading platforms, and customer data to maintain compliance and trust.
Government & Defense
Secure critical applications, APIs, and cloud environments by mapping cryptographic assets and ensuring post-quantum readiness.
Healthcare & Life Sciences
Protect sensitive patient and research data by discovering and upgrading vulnerable encryption before it becomes exploitable.
Technology & Infrastructure
Safeguard classified and mission-critical systems from future quantum threats through complete cryptographic visibility and control.
// Why Now //
Why Post-Quantum Readiness Can't Wait
A cryptographic inventory is quickly becoming table stakes for PQC migration and compliance. With HNDL, adversaries can harvest today and decrypt tomorrow—organizations must act now to protect their cryptographic estate.

Harvest Now, Decrypt Later Threat
Nation-state actors and sophisticated adversaries are already intercepting and storing encrypted data today with the intent to decrypt it once quantum computers are capable of running Shor's algorithm.

Compliance Requirements
NIST has finalized post-quantum algorithms, and regulations are emerging that will require organizations to discover, inventory and assess their cryptographic assets to ensure they are compliant.
// Get in touch //
Let’s Future-Proof Your Encryption
You can’t protect what you can’t see. Let Qinsight give you the visibility to take control of your cryptographic future.


How Qinsight Delivers Enterprise Cryptographic Management Capabilities
Qinsight’s platform was specifically designed to address the challenges of migrating to post-quantum cryptography through advanced discovery, classification and risk management features.

Enterprise Cryptographic Asset Discovery
Qinsight continuously collects cryptographic signals across your estate — TLS/SSH, certificates, keys, and libraries—under your scope and control to reveal your true footprint.

Cryptographic Bill of Materials (CBOM)
Findings are normalized into a searchable CBOM with algorithms, key sizes, certificate chains/issuers/expirations, protocol/cipher details, systems, and owners — ready to tag and export.
Compliance & Risk Management
Policy checks flag weak/expired/non-standard crypto, deprecated protocols, short keys, and quantum-susceptible usage. Get a PQC readiness score, and export compliance-ready reports (CSF 2.0, DORA, NIS2).



